Mobile apps have, to date, shaped our daily lives considerably, restoring themselves to varied goals for rapid communication and entertainment. Nevertheless, the road to mobile app development Dubai carries along the two edges of security. Security is the main concern of app developers UAE at each stage of the development of complex mobile applications. Developers need to secure user data, defend against vulnerabilities, and use this to foster user trust. In this detailed guide, we will explore the fundamental security rules and best-practices that developers should orient themselves towards. This will be useful to have comprehensive mobile application security.
If you want to survive in the mobile world, your mobile app development company Dubai must scrutinise the risks and diligently enact countermeasures.
Mobile-Specific Security Challenges
Mobile apps exposed to numerous security vulnerabilities such as data leakage, insufficient protection, malware compose a formidable challenge to mobile developers. Mobile devices are different from each other due to their characteristics like portability, network connectivity and user interface. App developers Dubai must take these specific constraints into account and ensure the proper delivery.
Impact of Security Breaches
A problem with security of mobile app development that often surfaces could lead to severe consequences. These could range from major data leakages to financial loss, reputational damage, and legal actions. Given the rather confidential nature of information being held and used by mobile applications Dubai, security becomes significant. The role of high end security measures for the sake of information integrity may, therefore, be considered absolutely crucial.
Primitive Security Steps
Secure Coding Practices
The safety of mobile apps stems firmly on the adherence to secure coding practices, being the bedrock foundation. Application developers Dubai should adhere to best practices by assuming that inputs are not secure. They must secure their data with strong authentication mechanisms and handle errors properly in order to resolve common vulnerabilities. These might include injection attacks, broken authentication and insecure data handling.
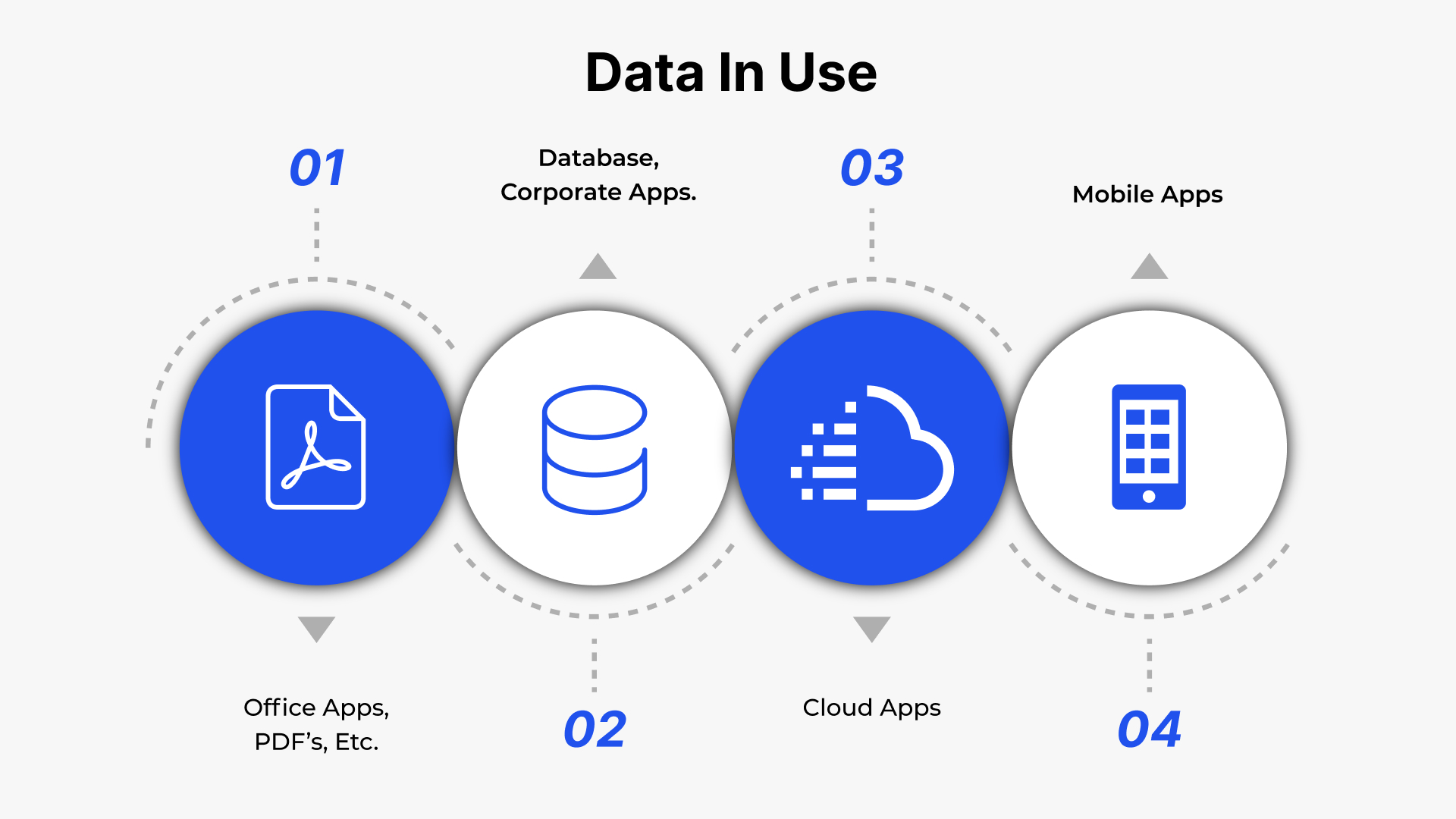
Data Encryption and Storage
The security of such sensitive data that is stored on mobile devices and communicated over different networks guarantees safety. It keeps data encrypted to prevent unauthorized access.
Prioritizing strong encryption algorithms to data at rest and in transit as well as key management is an essential aspect. Mobile apps development companies emphasize it when it comes to user information security from any hack.
Secure Network Communication
Frequently, network communication takes place to get the content of mobile application development from the server. It can also work with external services for mobile app development. Where transmission of data is entered, secure communication protocols like HTTPS and TLS/SSL must be applied in order to prevent eavesdropping, man-in-the-middle attacks, and data tempering.
User Authentication and Authorization
Powerful user authentication and role-based mechanisms are essential to ensure that only allow access to selected features of app development. It regulates access for the users and the app data. Implementation of multi-factor authentication, secure password policies and session management can strengthen app development Dubai so that accounts aren’t compromised.
Secure Backend Services
The security of apps into the mobile environment is not only the client side approach. In the backend, services should include API as well as the server infrastructure, which would be made as secure as possible by input validation, rate limiting, and access controls in a bid to reduce attacks that target the server-side elements.
Code Obfuscation and Minification
The minification and the code obfuscation are among a range of techniques to make reverse engineering and unauthorized code attribution difficult. These steps bring more difficulties in a way that bad actors can not understand the app and modifying the code, hence we improve the reliability of the app against counterfeiting and intellectual theft.
Modes of Regular Security Auditing and Testing
Since the falsification of vulnerabilities in the app is one of the major problems, the security assessment that includes the penetration testing and the code review process becomes imperative. Continuous security testing throughout development time, both pre-release and post-release, is an excellent security proactive step that guarantees timely addressing of security flaws and superiority of the app to existing attacks.
Pro Tip: Jot down the process of safe deployment and maintenance with the objective of creating a list of the most effective security measures.
Timely Patching and Updates
It is imperative that the app and its dependencies are upgraded to ensure the latest fixes and security patches are available therefore this allows for known vulnerabilities to be addressed. Immediately updating on the libraries, frameworks, and operating system components’ security vulnerabilities limits the scope of attackers looking for exploits that are already proven.
App development Dubai must disclose and notify all permissions and adhere to data protection regulations. Ensuring users' privacy and following up on users' permissions is pivotal in gaining the trust of app users. Mobile app developers Dubai must be guided by the principles of the least privilege. Here, end-users will be informed of the purpose of data collection and that it will be collected in compliance with regulations. These involve user data privacy regulations such as GDPR and CCPA.
Secure Offline Functionality
Mobile applications development in Dubai frequently runs in offline or in intermittent network environments. Introducing secure offline functionality such as encrypted local storage and secure data synchronization across devices gives security assurance. It makes sure that these devices remain protected even when they are offline.
Response to Security Incidents
Having an efficient and well planned incident plan will aid developers to deal with security breaches and data incidents. By setting up explicit guidelines for incident identification, confinement, and communication, the magnified effect of a cybersecurity incident will be reduced while a smooth and timely reaction will be facilitated.
Mobile App Security: A Look at Future Drivers and Implications
Mobile Threat Defense Solutions
Through the addition of mobile threat remedy solutions as well as capabilities, such as application shielding, behavior-based anomaly detection and endpoint security, the role of defence against advanced and targeted attacks is to become a key in successful mobile app security.
Zero-Trust Architecture
Zero-Trust architecture for mobile apps development Dubai involves constant monitoring, micro-segmentation, and access control. It also covers risk assessment, end-to-end encryption, logging and auditability.
Implementation of the zero-trust security standard holds that nothing can be treated as there is no implicit trust for anything. This serves as the most relevant for security in mobile apps development Dubai. Enabling granular access controls, continuous authentication, and stricter checks on user and device identities is of huge importance. It signifies completely secure app development Dubai following the zero-trust ideology.
Blockchain for improved data integrity improvements.
The application of the blockchain technology constitutes a new avenue destined to ensure the reliability and inviolability of data in the mobile applications. Employing blockchain for the execution of attempts such as secure transactions, identity verification, and audit trails can be an effective means to improve mobile application security posture.
Upholding Security and Privacy with DXB APPS
DXB APPS is the most reliable outsourcing service provider, taking the lead among mobile app development companies in Dubai. The company personifies a user-centric process that it depends on in app design Dubai. Additionally, we enrich user experience to provide marketable apps that are not only functional but also scalable. DXB APPS accommodates a professional team committed to the delivery of the most innovative, tailored apps.